Did the census really suffer a denial-of-service attack?
PM Malcolm Turnbull has today acknowledged there were serious failures in preparations made for the census. So with continued confusion over what exactly happened to the website, tech expert Mike Johnstone examines the possible scenarios.
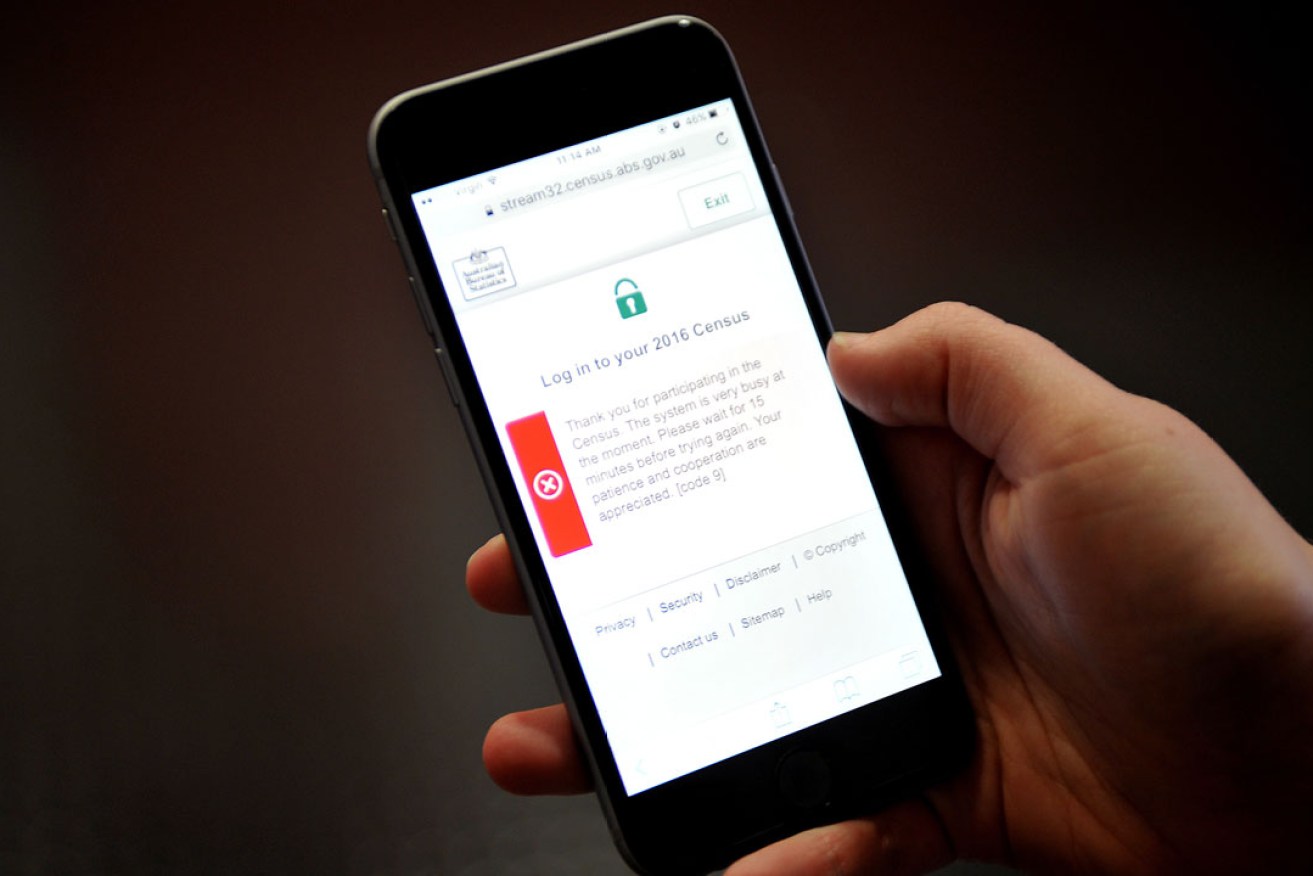
The error message seen on the Australian Bureau of Statistics census website. Photo: AAP
On Tuesday night, the Australian Bureau of Statistics (ABS) closed the 2016 Census website. No explanation was given at the time, except for a message on the page saying “the system is very busy at the moment”.
Yesterday morning, the ABS’s head statistician, David Kalisch, announced that the site had been brought offline by four distributed denial-of-service (DDoS) attacks.
The minister responsible, Michael McCormack, later qualified these statements by stating the site was not “attacked”, per se. While this is a semantic quibble, it is accurate in the sense that a DDoS “attack” in itself is not an attempt to gain access or subvert information.
The Prime Minister’s cyber security advisor, Alastair MacGibbon, added that a number of technical issues compounded the effects of the attack, including the failure of the ABS’s geoblocking system at around 7.30pm, which allowed the DDoS traffic to impact the ABS servers, hosted by IBM.
However, it has also been pointed out that the ABS may simply have been unprepared for the volume of traffic it received on census night.
So how plausible is the claim that the census was brought down by a DDoS attack?
Attacking availability
Confidentiality, integrity and availability are the basic principles of information security.
Cyber attacks are commonly mounted against each of these principles, with the ABS claiming that its server availability was the target on Tuesday night.
A conventional attack against availability is denial-of-service (DoS). A DoS attack occurs when a system (such as a website) is flooded with carefully crafted requests such that requests from legitimate users cannot be serviced, thus causing the “denial” of service.
A DDoS, or distributed DoS, occurs when many systems are used to perform a DoS attack on a target. This makes it harder to counter, as the server operator cannot simply block a single system on the internet that is sending all of the spurious requests.
Thus a DDoS is like many ants bringing down an antelope by working together.
The systems that are used to carry out the attack might be home computers connected to the internet that are being used without the knowledge or consent of their owners.
This can happen when a user clicks on a link contained in an unsolicited email that appears to be from a genuine party that the user trusts. Such email can be very sophisticated and appear realistic, so it is easy to be tricked.
The link then downloads software that allows a third party to initiate a DoS attack remotely, using the unfortunate user’s computer. When the third party has enough computers under their control (known as “zombies”), they can launch a DDoS attack from afar.
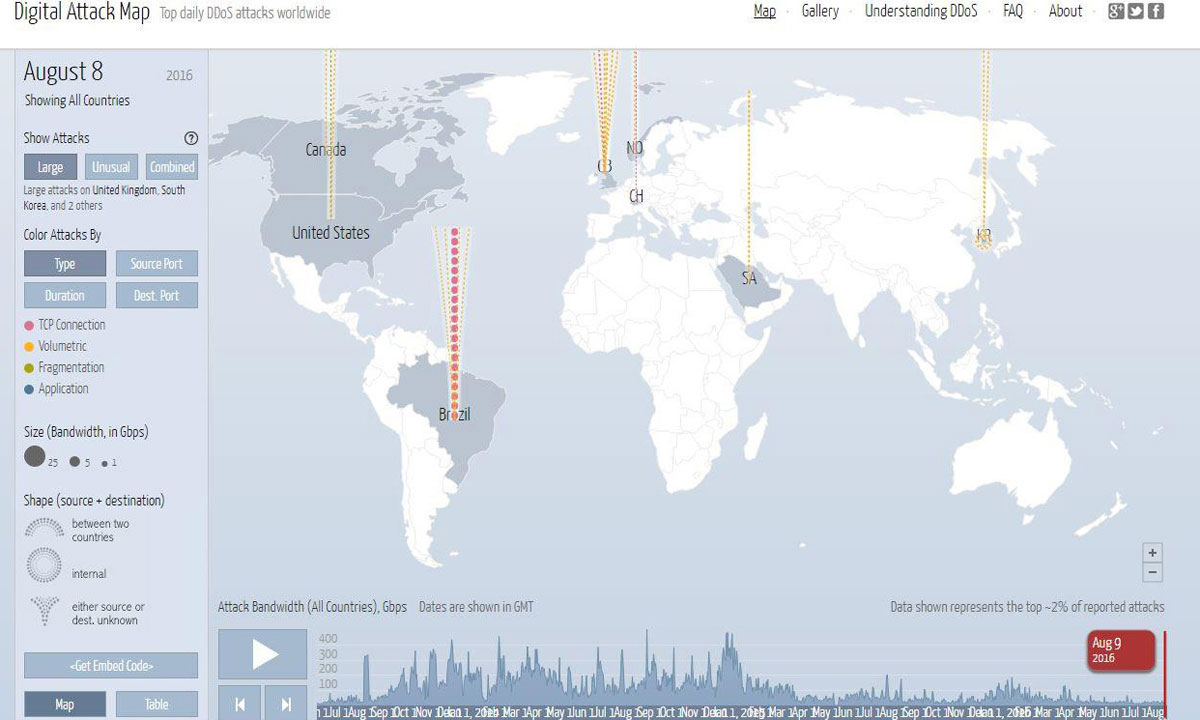
A screenshot of global Distributed Denial of Service (DDoS) attacks on Tuesday, showing no evidence of an Australian-targeted attack. Photo: AAP
DoS attacks were once solely the realm of experienced hackers with detailed knowledge of the inner workings of the connected computer systems. Recently, the resources needed to perform a DoS attack have been made readily available on the internet, so people with little knowledge of the technicalities could perform an attack.
Such attacks are now available anonymously as a “service”, much as many businesses use cloud services for computing power or data storage.
Therefore, this capability is available to a range of potential attackers, from lone-wolf disgruntled individuals, to activists, to interest groups and even nation states.
Websites are attacked every day. However, cyber security professionals already use a range of techniques to prevent or minimise such attacks.
One such is geoblocking, which prevents traffic from overseas from reaching the server. And it was the geoblocking system that apparently failed on Tuesday, allowing the DDoS to hit home.
Was it a DDoS?
The census servers were not actually hosted by the ABS but by IBM, a company with extensive experience of running server networks.
The ABS also spent around $470,000 load-testing its census servers in anticipation of census night. It claimed to have tested the system to 150 per cent of the expected load, saying that it could handle 1 million form submissions per hour – twice what the ABS expected it would need.
However, that might have under-estimated the kind of load the servers should have expected.
Consider that there were 12.9 million internet subscribers in Australia at the end of 2015 (according to ABS figures, no less).
If each of these represents a household (a reasonable assumption, given that 99.3 per cent of internet connections are broadband) and 2 million of these households accessed the census system during the day, this leaves a potential 10.9 million households attempting to reach the census servers in the evening.
If only half of those households actually attempted to fill out their census form on Tuesday night, that still would have exceeded the ABS’s anticipated submission rate.
There is also the issue of how it conducted its load-testing, and whether it worked around average numbers per hour or considered peaks in activity.
While the ABS may have attempted to anticipate the traffic on census night, there are indications that it didn’t consider all of the possible bottlenecks. Security journalist Patrick Gray also quotes a security professional’s analysis of some of these bottlenecks.
There is also no evidence – besides the claims of the ABS and Minister McCormack – that the census servers suffered a DDoS. One website that tracks DDoS attacks globally showed no unusual activity in Australia around the time of the census, although such websites are not 100 per cent accurate.
So while it’s possible that the census servers did suffer a DDoS attack, the evidence that it actually happened is inconclusive.
However, if the servers were already struggling under the load caused by Australians filling out their census forms, then even a weak DDoS could have been sufficient to tip it over the edge.
This leaves us with three possible scenarios:
1) A DDoS attack caused the problem;
2) Too many users overloaded the system; or
3) A combination of both.
Perhaps we should apply Occam’s razor and look for the simplest explanation. This would suggest that if it’s probable the Census servers simply failed under the weight of their task, then that’s the most likely explanation, rather than a deliberate DDoS attack.
Mike Johnstone is a security researcher and senior lecturer in Software Engineering at Edith Cowan University. This article was first published on The Conversation.




